Introduction
(Updated 8/18/24)
See Neil’s related video on YouTube
The main communication points from ISACA (the custodian of the CMMI) are:
- A new model architecture to reduce the time and resources it takes to make updates
- New Practice Areas (PA) covering safety, security, data management, staff development, and virtual delivery
The main changes in Version 3 are:
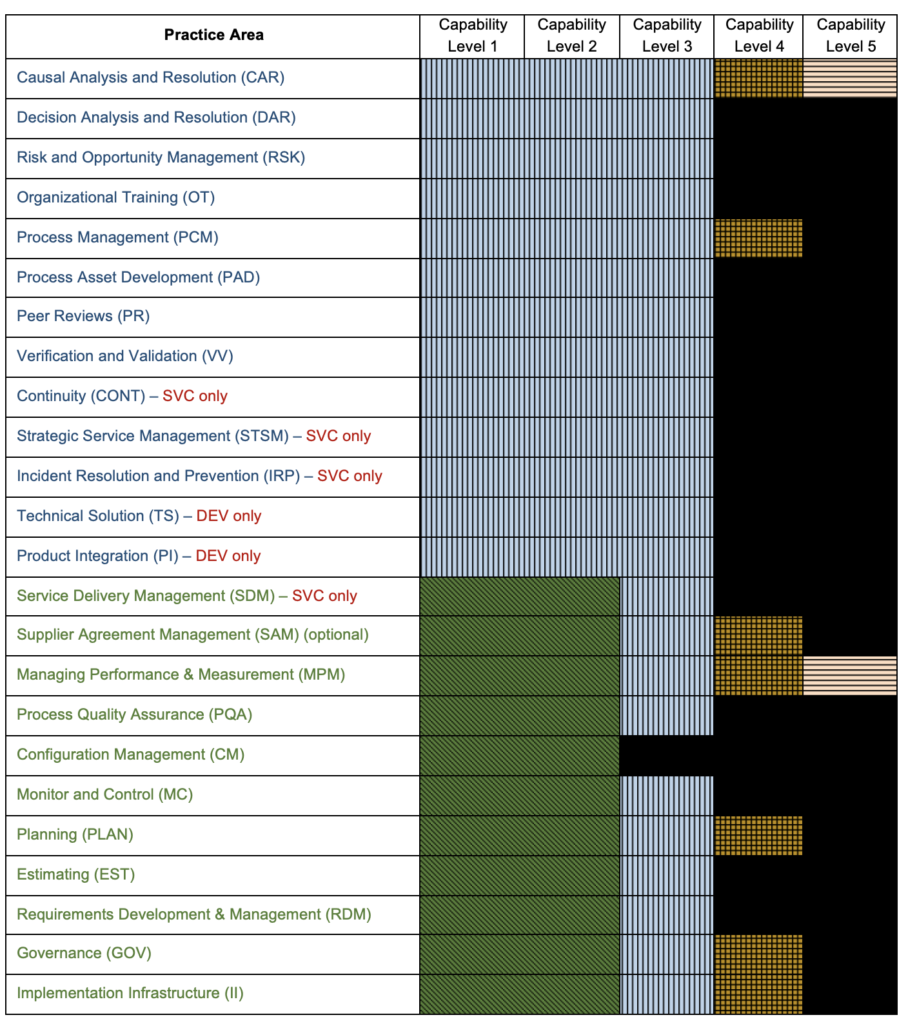
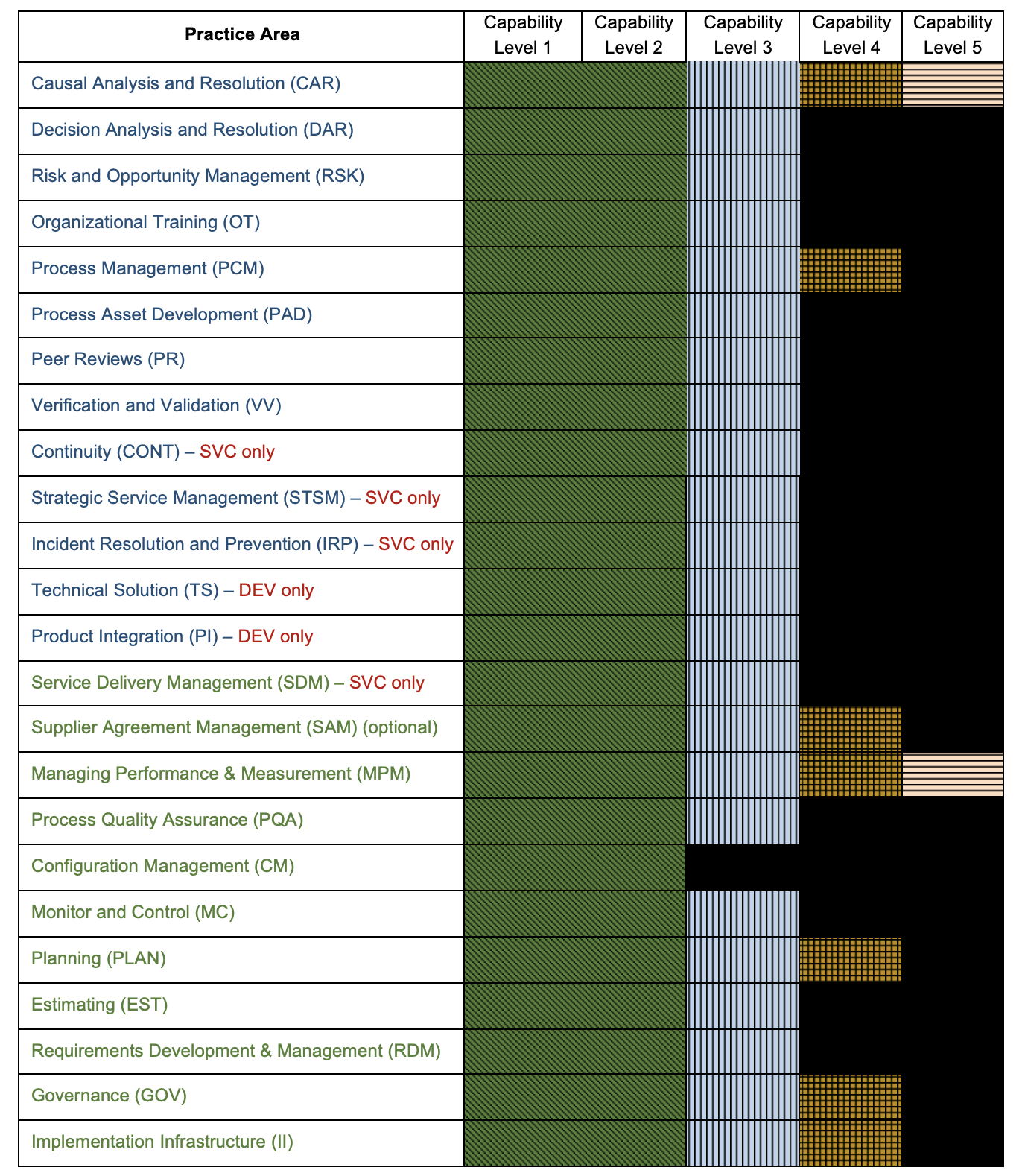
- Maturity Level 2 is now defined as all Practice Areas at Capability Level 2; this a major change in philosophy
- Supplier Agreement Management has two additional practices for supplier selection (from a previous model version)
- The new PAs (described below)
All the other Practice Areas in the Development and Services model remain unchanged apart from some minor wording updates.
The New Definition of Maturity Level 2
Figures 1 and 2 (below) show Maturity Level 2 in the old and new versions.
The reason for the change is that ISACA thinks of the model now as a methodology for performing work defined at different levels of process maturity, rather than a maturity model that defines priorities for improvement. The model was originally intended as a maturity model that guided an organization on what practices to master before taking on more advance practices (e.g., mastering estimation and commitments before mastering design). The rationale was that unless you have good planning in place, there will be little time for tasks such as design, since the project will end up as a death march without a plan.)
Figure 1 — Green Block = Maturity Level 2 in CMMI Version 2
Figure 2 — Green Block = Maturity Level 2 in CMMI Version 3
An example version 3 argument would be as follows: Since all teams need to do design (substitute any CMMI topic for the word design), make sure design is performed at each maturity level, even if that is Maturity Level 1 or 2. In version 3, process maturity is the improvement of all processes in parallel instead of focusing on project management and project scope management as a foundation.
How You Could Use V3 of the Model
Just because Maturity Level 2 has been redefined to include all PAs, it does not mean that you must adopt all PAs at once. You can still adopt them in the order you need based on the challenges you have.
Here are some examples of the order they could be adopted in.
- Focus first on the old ML2 Practice Areas to make sure projects are well managed
- Use process improvement planning (PCM Practice Area) to plan for model adoption. Start with a simple task list that defines what, who, and when
- Add risk and opportunity management (RSK) to your project planning activities
- Adopt peer reviews (PR) to find errors in requirements and proposals
- Run a causal analysis (CAR) on a few project successes and failures to see what you can learn
Changes in the Development and Services Model Practices
The changes in the DEV and SVC model practices are listed below. They are mostly very minor.
- CAR: Deleted the word “root” from “root cause.
- GOV: Minor word changes to practices 2.2, 2.3, and 4.1.
- II: Added new practice 4.1 – Develop the organizational capability to understand and apply statistical and other quantitative techniques to accomplish the work.
- MPM: Minor word changes to practices 3.5. 5.1, 5.2, and 5.3.
- OT: Minor word changes to practice 3.5.
- PLAN: Changed wording in 2.6 from “Ensure plans are feasible by reconciling available and estimated resources” to “Ensure plans are feasible by reconciling estimates against capacity and availability of resources.”
- PAD: Deleted practice 3.5 (“make assets available”) since it was redundant with practice 3.3. The new 3.3 practice is “Develop, keep updated, and make the organization’s processes and assets available for use in a process asset library.”
- PCM: Minor word changes to practice 3.6.
- RDM: Merged 2.1 and 2.3 into 2.1 which is now “Elicit stakeholder needs, expectations, constraints, and interfaces or connections, and confirm understanding of requirements.”
- SAM: Practices 2.1 and 2.2 have been brought back from earlier versions.
The new PAs are listed below.
New Available Practice Areas
The primary reason for CMMI V3 is to promote the PAs listed below. They are not required to be used.
- Data Management (DM)
- Data Quality (DQ)
- Enabling Safety (ESAF)
- Enabling Security (ESEC)
- Enabling Virtual Work (EVW)
- Managing Security Threats & Vulnerabilities (MST)
- Workforce Empowerment (WE)
Each one is based on the format, Plan X, Do X, Check X, and Act on the results of X. The downside of this is that you could define X to be trivial and then appraise Maturity Level 3 with a trivial implementation. Only time will tell to see who adopts them.
If you decide to include one or more of these in a CMMI appraisal, the appraisal team will need to take a new four-day Building Organizational Capability class that covers all Practice Areas and take the new Practitioner exam.
This new class option is additional to the existing classes, Foundations of Capability (two days, covering the core PAs) and Building Excellence (e.g., 1-day DEV and 1-day SVC class). These existing classes will be updated to cover changes in the DEV and SVC models.
Paths Forward
You have two basic paths to choose from:
A) If you are planning on a DEV or SVC appraisal, then:
- Existing appraisal team members (ATM) who are trained in CMMI V2 only need to pass the Associates exam when their certification expires after three years. The new exam will cover some of the V3 changes, so work with your LA to learn about them.
- New appraisal team members (who have not taken a CMMI V2 Foundations and DEV/SVC class) need to take the appropriate classes and pass the Associates exam.
B) If you are planning on appraising one or more of the new PAs, then the appraisal team will have to:
- Take the new 4-day Building Organizational Capability class and pass the new Practitioner exam. The class will be offered through your Lead Appraiser (LA) if the appraiser has chosen to pursue the new PAs.
- Verify appraisal team member domain experience. The ATMs will still be subject to the experience requirements for an appraisal. For example, if you are on a Data Management appraisal, the team will need 15 years of domain (Data Management) experience, and only one team member can have less than 2 years of experience. This might become a challenge to find the right people for the team. LA years of experience are not used in the calculation.
The LA will need between five and eight years of experience in the selected domain to qualify as an LA for that domain, and that might eliminate many LAs from getting certified to lead these new appraisals.
Appraisal Method Changes
- SAM is optional. SAM is in the Supplier domain, and selecting more than one domain is optional. SAM is a really good idea to protect your interests from bad suppliers, but the appraisal team has to take the 4-day Building Organizational Capability course and pass the larger 4-hour Practitioner exam. Most teams don’t want to do this.
- There are no other major changes to the appraisal method in V3.
Conclusion (Neil’s and Mary’s Opinion)
- The new definition of ML2 is a shift in what the original model was intended to be.
- Not many organizations target ML2 so it will not present a challenge very often. Groups that were going to target ML2 might now target ML3 since all the PAs have to be addressed.
- Neil and Mary don’t plan on pursuing the new PAs since we really have no expertise in them and don’t think the demand will be very high.
Please feel to contact us if you need help improving or navigating CMMI.
[Forward this email to your boss! Subject: CMMI V3 changes] Quick Link
Version 3 New Practice Areas
Data Management (DM)
Data Quality (DQ)
Enabling Safety (ESAF)
Enabling Security (ESEC)
Enabling Virtual Work (EVW)
Managing Security Threats & Vulnerabilities (MST)
Workforce Empowerment (WE)
 The Process Group helps you improve your organization's capability to routinely meet deadlines and delivery quality expectations. We are certified CMMI appraisers / trainers and Certified Scrum Masters.
The Process Group helps you improve your organization's capability to routinely meet deadlines and delivery quality expectations. We are certified CMMI appraisers / trainers and Certified Scrum Masters. 